
FinTech companies face a fundamental tension: they need to move fast to stay competitive, but they also need to meet increasingly complex regulatory requirements. The infrastructure powering financial applications must be robust, scalable, and compliant with stringent security, privacy, and operational resilience standards that continue to evolve in 2025. From PCI DSS and SOC 2 compliance to newer regulations like DORA and MiCA, development teams must navigate a maze of requirements while maintaining the agility to innovate. The key is building infrastructure that embeds compliance into the development process rather than bolting it on as an afterthought.

Convox offers a platform that simplifies the deployment and management of applications while helping maintain compliance. Here's how Convox can be used to meet various regulatory requirements:
Network security is the foundation of a compliant FinTech infrastructure. Convox makes it easy to create secure, isolated environments with zero-trust principles:
# Example convox.yml with security configurations
services:
api:
port: 3000
internal: true # Makes service accessible only within the Rack
web:
port: 8080
environment:
- API_URL=http://api.app.convox.local:3000By setting internal: true, you create services that aren't exposed to the public internet, establishing a secure network boundary. This configuration supports the principle of least privilege—a key requirement for frameworks like PCI DSS and the new DORA regulations.
For AWS deployments, enhance security further with:
# Enable private networking for your Rack
convox rack params set private=true -r production
# Configure more restrictive security groups for specific services
convox rack params set nlb_security_group=sg-01234567 -r production
# Enable AWS Pod Identity for fine-grained IAM permissions
convox rack params set pod_identity_agent_enable=true -r productionProtecting sensitive financial data requires comprehensive encryption strategies and privacy controls to meet 2025 standards:
Convox automatically provisions and manages SSL/TLS certificates:
services:
web:
domain: secure.fintech-app.com
port: https:8080 # Use HTTPS for end-to-end encryption
certificate:
duration: 2160h # Configurable certificate renewal periodFor internal communications that require encryption:
services:
db-service:
port: https:5432
internal: true
Convox Workflows provide a powerful way to integrate security throughout your CI/CD pipeline directly from the Convox Console, aligning with 2025's heightened security requirements.
In a highly regulated environment like FinTech, controlling who has access to what resources is critical. Convox provides robust access control mechanisms to help maintain compliance:
Convox's RBAC features allow for granular permission management based on specific roles and policies:
For example, you might create roles like:
For integrating with external CI/CD systems while maintaining security, Convox Deploy Keys provide a secure authentication method:
$ env CONVOX_HOST=console.convox.com CONVOX_PASSWORD=<deploy-key> convox deploy
$ env CONVOX_HOST=console.convox.com CONVOX_PASSWORD=<deploy-key> convox run web bin/migrate
$ env CONVOX_HOST=console.convox.com CONVOX_PASSWORD=<deploy-key> convox env set NODE_ENV=production FOO=bar ... --replaceBy implementing these access controls, FinTech companies can ensure that only authorized personnel can make changes to infrastructure and applications, providing the audit trail needed for regulatory compliance.
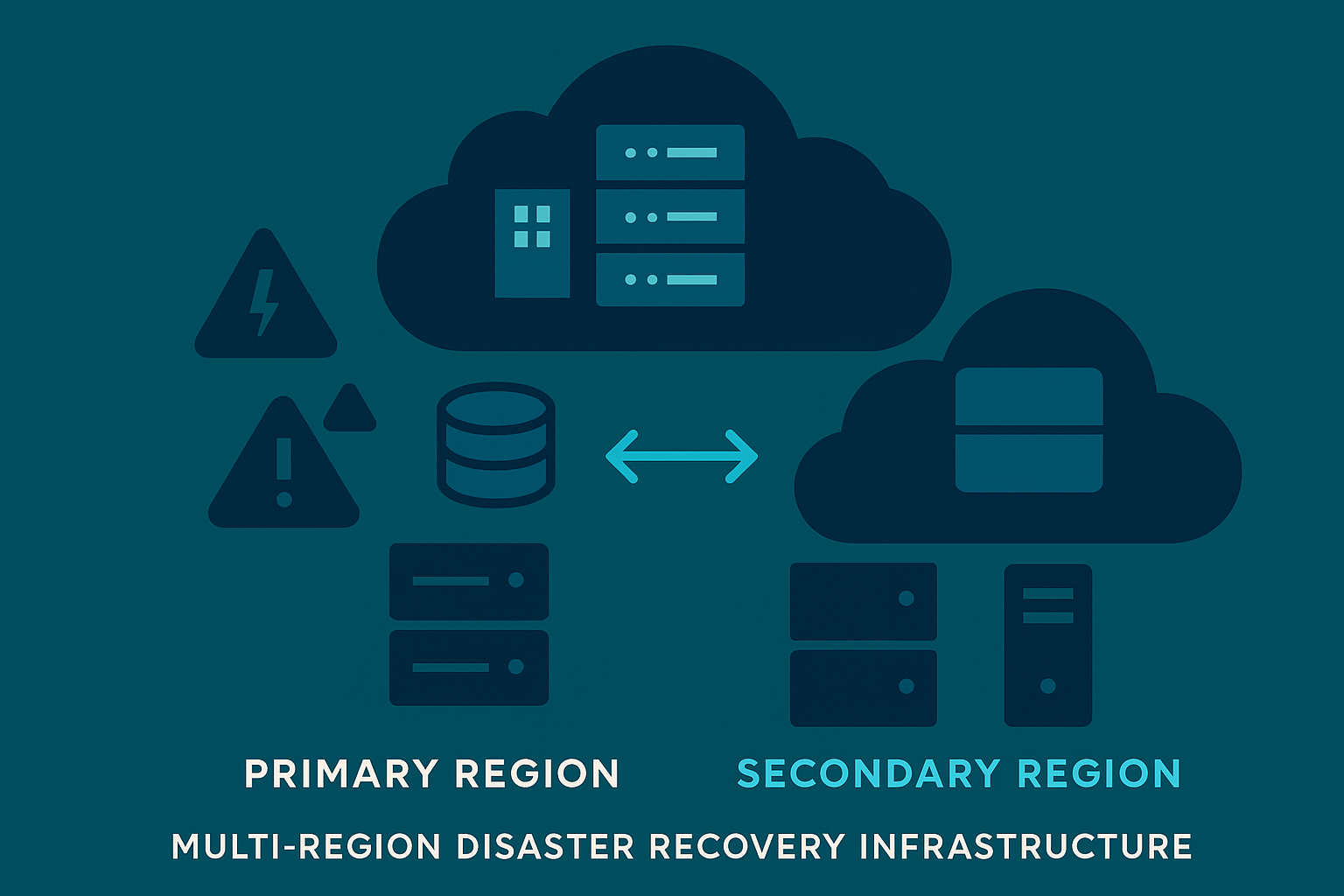
To comply with DORA's requirements for digital operational resilience, organizations can implement a multi-region disaster recovery strategy using Convox Racks.
efs_csi_driver_enable=true for durable storage# Configure minimal footprint for cost efficiency
convox rack params set build_node_min_count=0 -r dr-rack
convox rack params set min_on_demand_count=1 -r dr-rack# Add to your convox.yml
timers:
db-sync:
schedule: "0 2 * * *" # Daily sync at 2 AM
command: bin/sync-database-to-dr.sh
service: workerYour sync script would handle the logic for database dumps, transfers, and imports to the DR environment.
timers:
dr-test:
schedule: "0 1 * * 0" # Weekly test at 1 AM on Sundays
command: bin/dr-test.sh
service: workerThis multi-region approach satisfies DORA's requirements for operational resilience by providing geographically diverse infrastructure that can be rapidly activated in case of a regional outage, ensuring continuity of critical financial services.
Building compliant FinTech infrastructure in 2025 doesn't have to mean sacrificing developer experience or innovation velocity. With Convox, you can implement security and compliance controls while maintaining the agility your team needs to build cutting-edge financial products.
By following the strategies outlined in this playbook, you can create a secure, compliant infrastructure foundation that satisfies regulators while empowering your developers to focus on what they do best: building innovative financial solutions that meet the evolving needs of your customers.
Ready to build compliant FinTech infrastructure that doesn't slow down your team? Contact us to learn how Convox can help, or get started free today.
