
If you work in healthcare, government, or financial services, you already know that cloud adoption comes with strings attached. Your security team has a checklist. Your compliance officer has questions. And somewhere in the background, an auditor is waiting.
The promise of the cloud has always been faster deployments and reduced operational burden. But for organizations handling PHI, FedRAMP workloads, or PCI-scoped data, that promise often collides with a harder reality: compliance requirements that demand isolation, audit trails, and control over every layer of infrastructure.
This is where most teams hit a wall. You can go fully managed and lose visibility into where your data lives. Or you can build everything yourself and spend half your engineering cycles on infrastructure instead of your product.
Convox offers a third path. It is an open-source Platform-as-a-Service that installs directly into your own cloud account, giving you Heroku-style deployment workflows while keeping your data exactly where it needs to be: under your control.
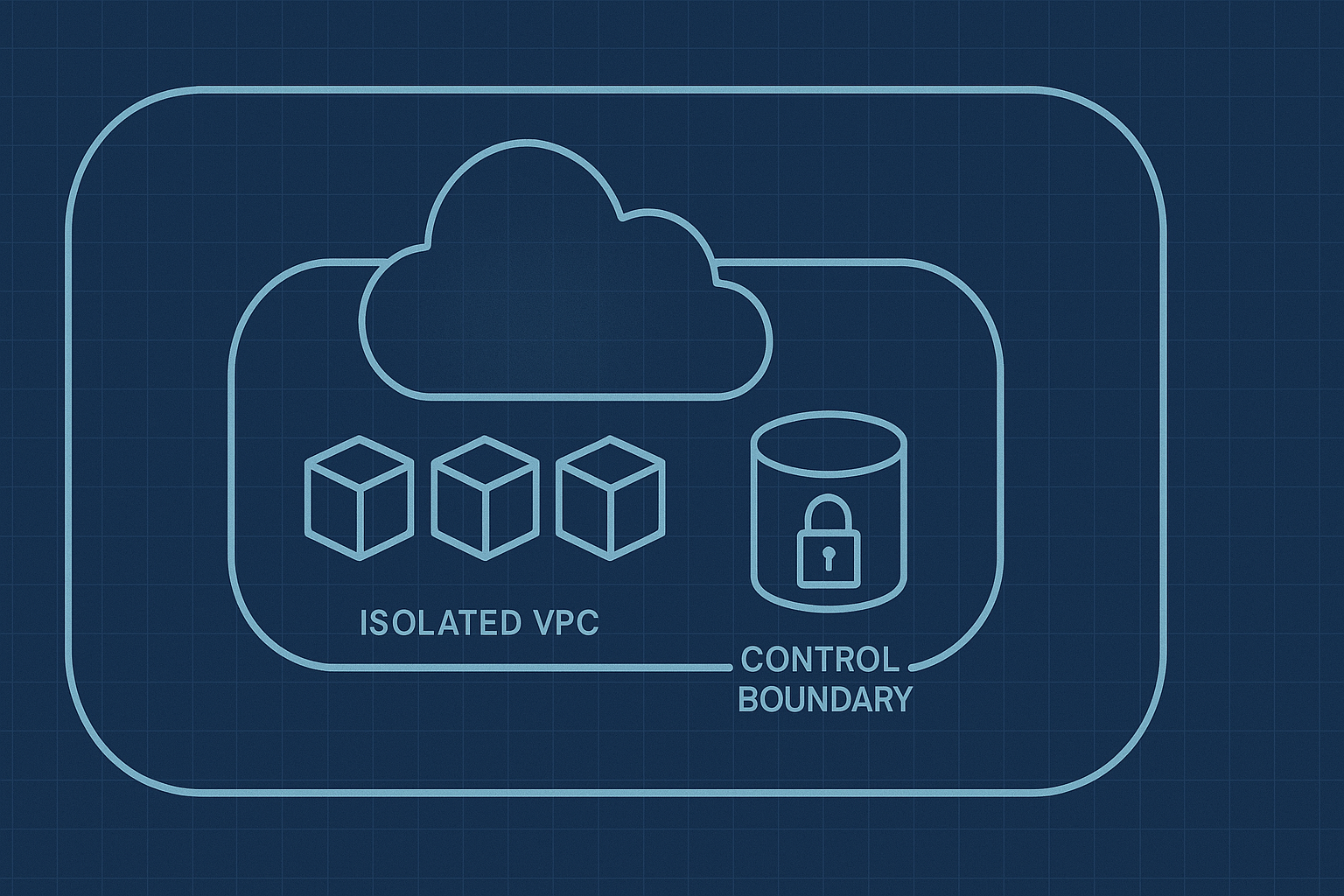
Compliance requirements vary by industry, but the underlying challenges are remarkably similar.
Healthcare teams handling PHI must satisfy HIPAA's administrative, physical, and technical safeguards. This means encryption everywhere, access controls, audit logging, and often isolation from shared infrastructure. Many organizations also pursue HITRUST CSF certification, which has become the de facto standard for demonstrating security maturity in healthcare. HITRUST maps controls from HIPAA, PCI-DSS, ISO 27001, and NIST 800-53 into a single certifiable framework, giving covered entities and their business associates a structured pathway to compliance.
Government agencies and contractors face FedRAMP requirements that mandate specific cloud environments. FedRAMP High workloads typically require AWS GovCloud or equivalent isolated regions. These environments have different service endpoints, ARN formats, and networking constraints that can force teams to maintain separate infrastructure code for commercial and government deployments.
Financial services organizations must navigate overlapping requirements from PCI-DSS, SOC 2, and regional data protection regulations. These controls demand encryption, immutable audit trails, strict access management, and the ability to demonstrate exactly how data flows through your systems.
Across all these industries, the common thread is control. You need to know where your data is, who can access it, and what changed and when. Traditional SaaS platforms often cannot provide the visibility or isolation these requirements demand.
Convox Rack is a self-hosted deployment platform that runs entirely within your own AWS, GCP, or Azure account. When you install a Rack, Convox provisions a complete infrastructure stack: a dedicated VPC, container orchestration (EKS on AWS), load balancers, certificate management, and logging. All of this runs on resources you own and control.
This architecture matters for compliance because it shifts the trust boundary. Instead of sending your workloads to a third-party platform, the platform runs inside your environment. You control the encryption keys. You own the VPC configuration. Your IAM policies govern access. For HIPAA scenarios, this means Convox itself can be placed outside the scope of Business Associate Agreement requirements because Convox operators have no access to your PHI.
Every Convox Rack is a dedicated, isolated cluster. There is no multi-tenancy at the infrastructure level. Your applications run in their own VPC with private subnets, and all public traffic flows through load balancers that you configure. This isolation extends to data storage: your databases, object storage, and encryption keys remain in your account and never touch shared infrastructure.
For organizations pursuing HITRUST certification, this architecture simplifies the scoping conversation. Your assessors can evaluate your Convox environment as part of your own infrastructure rather than inheriting complexity from a shared platform.
Convox handles TLS certificate provisioning and renewal automatically. All traffic to your applications is encrypted in transit by default. Data at rest uses your cloud provider's native encryption services, with keys managed through KMS or equivalent services that you control.
For additional isolation, Convox supports private Rack deployments where all resources run in private subnets with no direct internet access. Outbound traffic routes through NAT gateways with static IPs, which simplifies firewall rules and IP allowlisting requirements. You can also run on dedicated EC2 instances if your compliance requirements demand hardware isolation.
Every deployment, configuration change, and user action in Convox generates a log entry. The platform maintains a complete release history, so you can see exactly which container image was deployed, when, and by whom. This audit trail is accessible through the CLI and console, providing the documentation auditors need to verify your change management controls.
For teams operating under FedRAMP or SOC 2, this built-in audit capability addresses control requirements around change tracking and accountability. You can export logs to your SIEM or centralized logging platform for retention and analysis.
Convox provides RBAC for both CLI and console access. You can assign fine-grained permissions to team members based on their role, ensuring that developers, operators, and managers see only what they should. Enterprise deployments support SSO integration through SAML and LDAP, connecting to identity providers like Okta or Google Workspace. Hardware-based 2FA with YubiKeys is also supported for environments requiring stronger authentication.
For government workloads requiring FedRAMP High authorization, Convox Rack runs in AWS GovCloud (US). This means you can deploy the same Convox workflows and tooling in an isolated region that meets the strictest federal requirements.
AWS GovCloud itself maintains a FedRAMP High Provisional Authority to Operate (P-ATO), covering the underlying infrastructure controls. By running Convox within GovCloud, you inherit these controls while maintaining the operational simplicity of a PaaS.

This approach avoids the common pain point of maintaining separate codebases for commercial and government deployments. Convox uses infrastructure-as-code (Terraform on most providers) with parameterized configurations, so adjustments for GovCloud's different endpoints and ARN formats are handled at the infrastructure layer rather than requiring application changes.
Convox offers two deployment models. Convox Cloud provides managed compute machines where Convox handles infrastructure provisioning and management. Convox Rack is the self-hosted model where you install the platform into your own account and retain full control.
For regulated workloads, Rack is the appropriate choice. It ensures that all data remains in infrastructure you own, under security policies you define, with audit trails you control. Rack deployments place Convox outside the compliance boundary because there is no data exchange with external systems. You maintain your BAA with AWS (or your cloud provider), and Convox functions purely as infrastructure automation running in your environment.
The operational benefit of Convox is that it handles the undifferentiated heavy lifting of cloud infrastructure while leaving you in control of everything that matters for compliance.
CI/CD is built in. Push code to GitHub or GitLab, and Convox builds, tests, and deploys automatically. Review apps spin up for pull requests, giving stakeholders and auditors visibility into changes before they reach production.
Deployments are safe by default. Rolling updates ensure zero downtime. Health checks verify containers are ready before traffic is switched. Rollbacks are instant if something goes wrong.
Scaling is declarative. Define your resource requirements in a simple YAML manifest, and Convox handles autoscaling based on load. No manual intervention required.
Infrastructure updates are automated. Convox manages Kubernetes control plane updates, applies security patches, and handles routine maintenance without requiring your team to track upstream releases.
This means your engineers spend time on your product rather than on infrastructure operations. And when the auditors arrive, you have the documentation, isolation, and controls they need to see.
If your organization is evaluating platforms for regulated workloads, the key questions to ask are: Where does my data live? Who has access to it? And can I demonstrate compliance controls to my auditors?
With Convox Rack, the answers are straightforward. Your data lives in your cloud account. Access is governed by your IAM policies and RBAC configuration. And the platform provides the audit trails, encryption, and isolation that compliance frameworks demand.
You can install a Rack through the Convox Console or CLI in under an hour. From there, deploying your first application is as simple as convox deploy. The same workflow scales from a small healthcare startup to a federal agency running FedRAMP High workloads in GovCloud.
For organizations pursuing HITRUST certification, planning a FedRAMP authorization, or maintaining PCI compliance, Convox provides a platform that meets you where you are: full control of your infrastructure, with dramatically less operational overhead.
For enterprise deployments, compliance-specific questions, or to discuss your requirements: sales@convox.com
