
It was 3 AM when Sarah, the lead DevOps engineer at a rapidly growing SaaS startup, received the dreaded alert. A junior developer, attempting to test some code changes on their staging environment, had accidentally deployed to production instead—overwriting critical configuration settings and causing an outage that affected thousands of customers.
The mistake was simple but devastating: the developer had been given overly broad access credentials that didn't distinguish between environments. With a single mistyped command, months of careful system tuning was erased, customer data was temporarily inaccessible, and the company's reputation took a hit they'd be recovering from for months.
This scenario plays out with alarming frequency across organizations of all sizes. According to a recent IBM security report, 95% of cybersecurity breaches involve human error, and misconfigured access controls represent one of the most common vulnerabilities. The problem isn't just external threats—it's also about protecting your infrastructure from well-intentioned internal mistakes.
Before diving into solutions, let's identify the most prevalent security anti-patterns that put organizations at risk:
Many teams rely on a small set of shared AWS or cloud provider credentials distributed among team members. This approach creates several critical problems:
Even when organizations move beyond shared credentials, they often fail to implement the principle of least privilege. Developers end up with excessive permissions because:
Credentials and sensitive configuration details frequently end up hardcoded in:
Many organizations implement stringent controls for production environments but leave development and staging environments relatively unprotected. This creates significant risks:
Without comprehensive logging and auditing, organizations struggle to:
Convox was designed from the ground up to solve these infrastructure security challenges. By building security into the platform's architecture rather than treating it as an add-on, Convox provides a "secure by design" approach to infrastructure management.
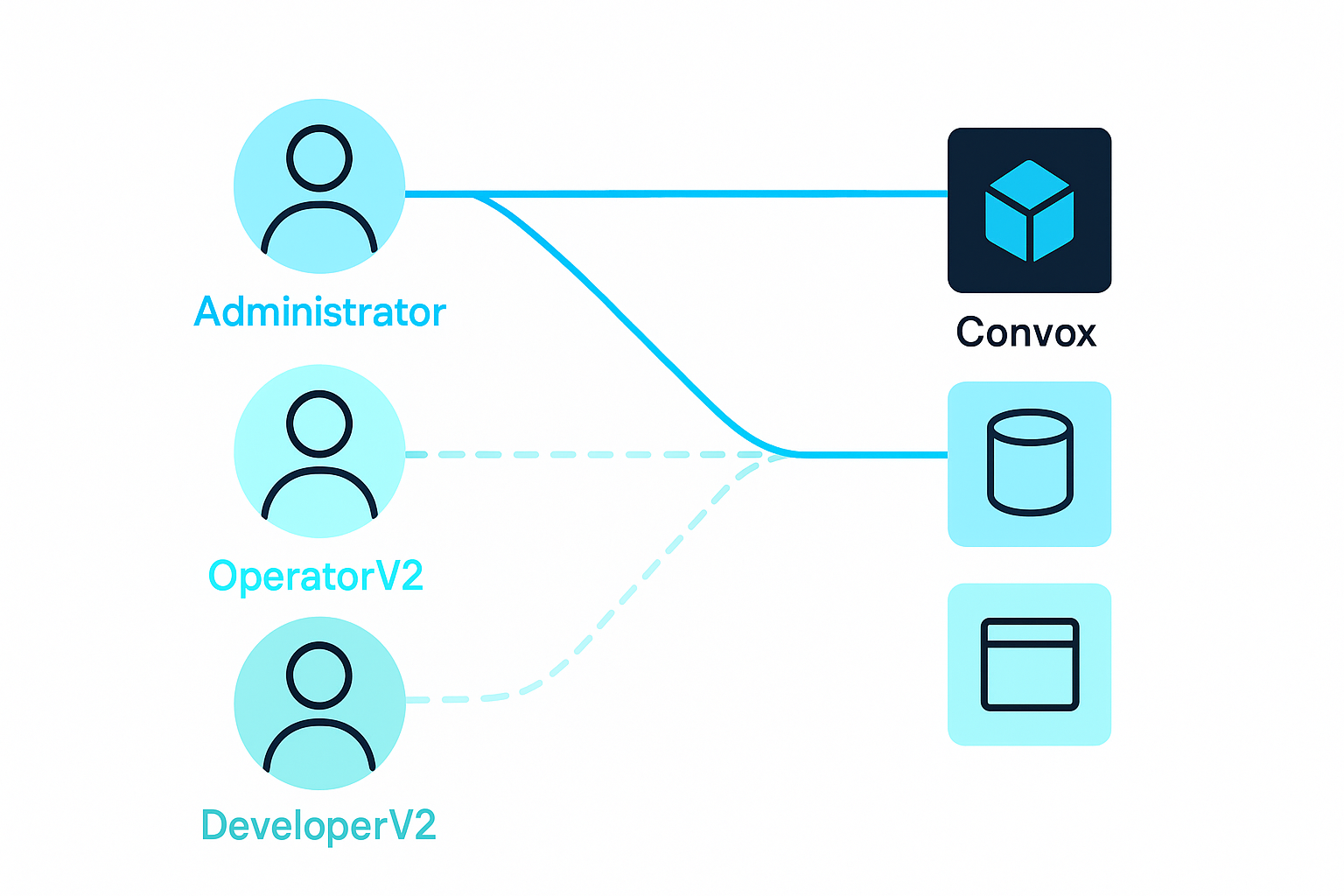
Convox implements sophisticated role-based access control through its RBAC system that allows organizations to define exactly who can access what resources and what actions they can perform:
This level of granularity ensures that everyone has exactly the access they need to do their job—and nothing more. A developer working on a specific application can deploy to development environments without having access to production systems or other applications.
Secure access begins with secure authentication. Convox seamlessly integrates with enterprise identity providers through its Integrations feature:
This integration ensures that when an employee leaves the organization or changes roles, their access can be quickly updated or revoked across all infrastructure resources, eliminating dangerous lingering access.
Convox provides a robust system for managing sensitive configuration and credentials through its Environment Variables feature:
Environment variables can be managed through either the CLI or Console:
# Setting environment variables via CLI
$ convox env set KEY=value
# Creating a new release with environment changes
$ convox env set FOO=bar -a myapp
Setting FOO... OK
Release: RABCDEFGHIConvox's Rack architecture provides natural security boundaries:
internal: true to be accessible only to other services within the Rackprivate: true parameter to run in private subnets by defaultThe architecture is configured through the convox.yml file, allowing clear definition of service access:
services:
web:
port: 3000
auth:
internal: true
port: 5000This architecture minimizes the attack surface and contains potential security incidents, preventing them from affecting other parts of your infrastructure.
Convox maintains detailed audit logs accessible through the Console:
The Console provides an intuitive interface to browse, search, and filter these logs, making it easy to investigate security incidents or conduct compliance audits. These logs provide invaluable information for security monitoring, compliance reporting, and incident investigation.
Additionally, application logs can be accessed via the convox logs command:
$ convox logs -a myapp
2020-01-01T00:00:00Z service/web/web-0123456789-abcde Starting myapp on port 3000Security isn't a one-time setup—it requires ongoing maintenance:
convox.yml manifestConvox makes updating your rack straightforward with a simple command:
$ convox rack update
Updating rack... OKAs documented in the CLI Rack Management section, you can also update to specific versions:
$ convox rack update 3.21.2
Updating rack... OKThis update process ensures that your infrastructure remains protected with the latest security patches and features.
Let's look at a practical example of how to implement secure access control using Convox.
Convox makes it easy to define roles through the Convox Console. According to the RBAC documentation, you can create and manage roles from the Users page:
The Console provides a user-friendly interface to define role permissions, where you can specify:
Convox offers pre-created roles that mirror the existing legacy Console Roles:
Administrator Role:
OperatorV2 Role:
DeveloperV2 Role:
These roles provide a secure foundation that can be customized to meet your organization's specific needs.
Deploy keys are limited scope API keys ideal for CI/CD pipelines. According to the Deploy Keys documentation, you create these through the Console:
These keys have restricted permissions and can only execute specific commands:
buildbuildsbuilds export/importdeployenv set --replacelogsrackracksreleases promote (only with a specified release ID)runWith RBAC, you can now assign custom roles to Deploy Keys, extending their default permissions for more flexibility.
Using a deploy key in your CI environment looks like this:
$ env CONVOX_HOST=console.convox.com CONVOX_PASSWORD= convox deploy
$ env CONVOX_HOST=console.convox.com CONVOX_PASSWORD= convox run web bin/migrate Convox integrates with enterprise identity providers through the Console:
Once configured, users can authenticate using their organizational credentials, and their access rights are determined by the roles assigned to them in Convox.
Convox provides comprehensive audit logs through the Console:
The audit logs track all significant actions including:
This visibility is crucial for security monitoring and compliance reporting, allowing you to track who performed what actions and when.

For organizations in regulated industries, Convox's security features help meet common compliance requirements:
Convox helps satisfy key SOC2 controls:
Healthcare organizations can leverage Convox for HIPAA-compliant infrastructure:
The traditional trade-off between security and developer productivity creates a false dichotomy. Organizations often believe they must choose between robust security controls that slow development or streamlined processes that increase risk.
Convox eliminates this trade-off by making security an integral part of the platform rather than an impediment to productivity. With Convox:
As infrastructure becomes increasingly complex and security threats more sophisticated, organizations need platforms that provide security by default rather than as an afterthought. Convox's "secure by design" approach ensures that even as your applications and team grow, your security posture remains strong.
By addressing the common anti-patterns in infrastructure security and providing integrated solutions for access control, authentication, secrets management, network isolation, and audit logging, Convox helps organizations build and deploy applications with confidence—knowing that their infrastructure is protected not just from external threats, but also from the well-intentioned mistakes that often cause the most damage.
Ready to strengthen your infrastructure security with Convox? Get Started Free today or reach out to our team at sales@convox.com for a personalized security assessment.
